Fast Hyperlinks
SafetyNet bypassing has lengthy been a cat and mouse sport between Google and the group. The group loves to change the software program on their cellphone, a course of that normally entails bootloader unlocking as step one. However this, in flip, journeys SafetyNet, which may trigger a number of widespread apps to cease engaged on the cellphone, a few of them understandably in order they depend on a tamper-proof atmosphere for execution.
SafetyNet is meant for app builders, however they’ll select to make use of it or not. For a daily finish person, although, you’ll be able to both surrender on the modding potential of Android and cross the SafetyNet compatibility checks, or keep ostracized by the app publishers. In case you’re questioning the right way to cross SafetyNet even after rooting or putting in a customized ROM in your machine, this information ought to allow you to with that.
What’s SafetyNet?
Android is designed to run with out giving the top person any form of privileged management over the underlying subsystems. In case an individual working an Android machine is ready to acquire related entry to administrative (AKA “superuser”) permissions as on Linux, they’ll basically alter or change Android system purposes and settings. From the attitude of an app developer, it means the machine their app is working on can probably be compromised. There must be some form of abuse detection system to look at the machine’s software program and {hardware} atmosphere and guarantee the app builders that the whole lot is alright. That is the place SafetyNet is available in.
Whereas modding is an integral a part of the Android ecosystem, typically you want a excessive diploma of rigor within the OS to fulfill the constraints of safety insurance policies. SafetyNet is such a set of abuse-detection APIs current within the Google Play Providers. By calling the SafetyNet Attestation API, third-party purposes can verify if the software program atmosphere of the machine has been tampered with in any means. The API checks for numerous issues just like the bootloader unlock standing, indicators of superuser binaries, and extra to match the present state of the goal Android machine and confirm the integrity of the atmosphere towards a recognized ‘protected’ worth on the server-side.
Notably, Google has already introduced plans to section out SafetyNet. It is going to be changed by the Play Integrity API by 2024.
SafetyNet tripping and its penalties
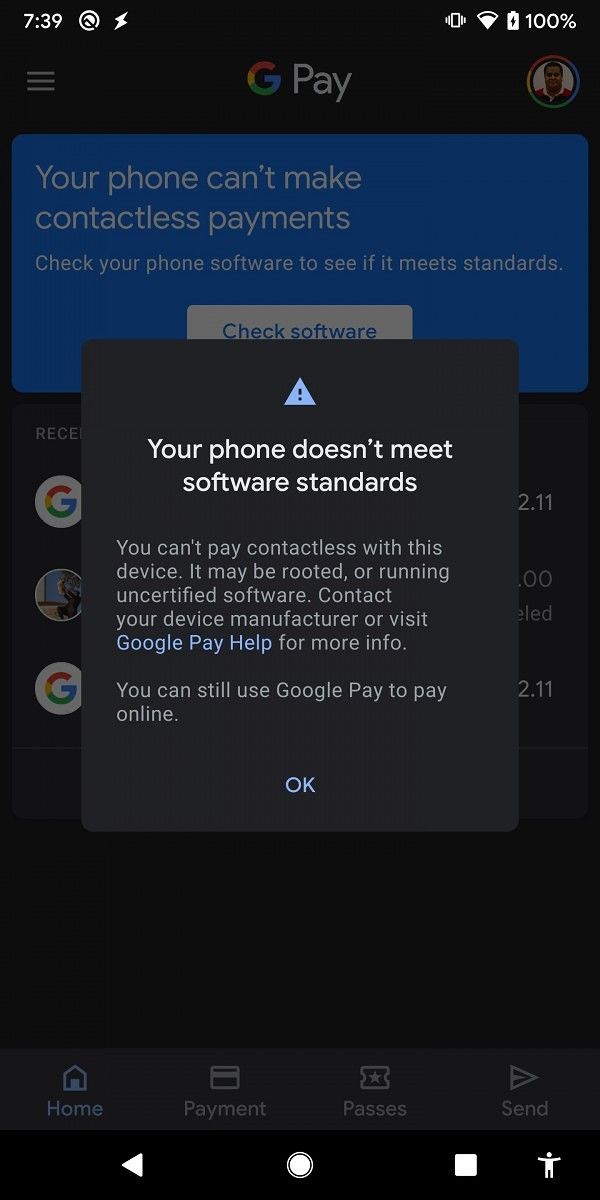
A lot of departure occasions from the inventory configuration of an Android machine ultimately result in SafetyNet tripping. Even if you happen to simply unlock the bootloader of your cellphone and depart the factory-installed OS untouched, you should still get a “CTS profile mismatch” (the place CTS stands for the Compatibility Test Suite) error that causes the SafetyNet verify to fail. In case you root your Android machine or change the inventory firmware with a customized ROM, you’ll just about find yourself with a SafetyNet failed standing. Consequently, you’ll be able to’t use apps and video games that make use of SafetyNet validation on the machine. That is very true for banking and different monetary apps comparable to Google Pay, as they strictly depend on the SafetyNet Attestation consequence and will not permit customers to function the app on a seemingly tampered atmosphere for the sake of safety.
On the subject of video games, builders use SafetyNet for assessing the machine’s integrity in order that they’ll forestall rogue gamers from dishonest or modifying in-game variables for unfair benefits. Final however not least, you may as well come throughout examples the place publishers are merely misusing Google’s tamper detection mechanism for no sensible purpose, which is why energy customers wish to evade the detection routines.
In a nutshell, the modding group must select between gaining access to root/customized ROMs/kernels/and so on. or their most popular apps and video games. This would possibly sound like the top of aftermarket improvement on Android, however there’s hope.
Easy methods to cross SafetyNet attestation on Android gadgets
Since Google periodically updates the spine of the SafetyNet Attestation API, there is no such thing as a true common methodology to bypass the checks. Because the restrictions rely on various elements, chances are you’ll cross SafetyNet on a modded atmosphere by spoofing probably the most important parameters on legacy gadgets, however the identical trick may not work in any respect on newer telephones. The aftermarket improvement group has provide you with various strategies for passing the SafetyNet checks, however remember the fact that a generic implementation is not potential as a result of ever-changing nature of the anti-abuse API. It is a sport of cat-and-mouse — someday you may be forward, the opposite day you’ll not be.
With the gradual transfer in the direction of the {hardware} attestation technique, Google is counting on the safety of the cellphone’s Trusted Execution Surroundings (TEE) or devoted {hardware} safety module (HSM) for tamper detection. Discovering a important safety vulnerability within the remoted safe atmosphere of a tool and exploiting it to spoof SafetyNet’s client-side response cannot be a possible method, however there exist different methods to get previous the impediment.
Listed here are among the well-known strategies to cross SafetyNet:
1. Restoring the unique firmware and relocking the bootloader
That is maybe the best option to cross SafetyNet, however it has its personal deserves and demerits. All it is advisable do is use the right firmware to your Android machine, flash it, and eventually re-lock the bootloader. In fact, you will lose a lot of the bells and whistles of Android modding, however it truly is sensible when it is advisable use your machine in a managed atmosphere with strict safety insurance policies otherwise you’re making an attempt to promote your machine.
2. Utilizing Magisk
In case you personal a legacy Android smartphone, Magisk is your greatest wager to cross SafetyNet with out a lot problem. Though the present secure construct of Magisk does not function MagiskHide anymore since v24, you’ll be able to nonetheless keep on with the v23.x model and make the most of MagiskHide to cover root standing from apps. Moreover, you’ll be able to set up Magisk modules like MagiskHide Props Config to vary the machine fingerprint with a purpose to cross SafetyNet.
Speaking in regards to the deprecation of MagiskHide, the brand new “DenyList” function of Magisk is an fascinating improvement, which permits customers to assign a listing of processes the place Magisk denies additional modifications and reverts all modifications it had accomplished. With an acceptable configuration, it will also be used to cross SafetyNet in some eventualities.
3. Utilizing Common SafetyNet Repair
Bypassing Google’s hardware-backed SafetyNet attestation method is a tad bit tough, however it’s not completely unattainable. The Common SafetyNet Repair undertaking by XDA Senior Member kdrag0n cleverly accomplishes this feat by forcing the essential attestation over the hardware-backed checks.
Notably, Common SafetyNet Repair has a dependency on Magisk on the subject of passing the essential attestation half. The developer helps Zygisk solely for the newest model, which implies you want Magisk 24 or newer to make use of it. That mentioned, you may as well discover Riru-compatible legacy builds within the repo linked beneath.
Common SafetyNet Repair: GitHub Repo ||| XDA Dialogue Thread
4. Shamiko
There’s additionally Shamiko — a work-in-progress module written on prime of Zygisk (Magisk within the zygote course of). It reads the listing of apps to cover from Magisk’s denylist to cover Magisk root, Zygisk itself, and Zygisk modules to bypass SafetyNet. Nonetheless, Shamiko can solely work after disabling the DenyList function.
You may obtain pre-release builds of Shamiko from the LSPosed’s GitHub repository.
5. ih8sn
In case you do not wish to depend on Magisk to cross SafetyNet attestation, you’ll be able to check out an experimental add-on named ih8sn. After making use of, it might probably spoof a plethora of prop values with a purpose to circumvent SafetyNet checks just like the MagiskHide Props Config module, however there is no dependency on Magisk within the first place.
The ih8sn instrument is maintained by a number of LineageOS builders, however the LineageOS undertaking does not formally endorse it but. It is not a ready-to-flash resolution, so it is advisable configure it your self earlier than flashing. To know extra, check out its codebase by following the hyperlink beneath.
Verification
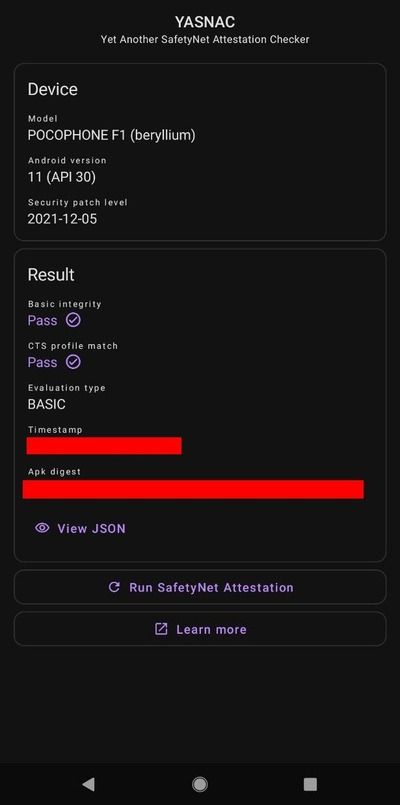
After making use of one of many aforementioned SafetyNet passing strategies, chances are you’ll want to confirm the consequence. The Magisk app comes with an choice to provoke the SafetyNet checking routine proper from its fundamental menu, which is basically helpful. You may as well go for an open supply app named YASNAC (quick for Yet Another SafetyNet Attestation Checker) to verify the standing and (optionally) study the JSON response.
That’s how one can cross SafetyNet in your cellphone. With just a little little bit of time and endurance, it’s potential to revive the true modding potential of Android with out bothering in regards to the SafetyNet Attestation failures. We’ll be updating this information with extra SafetyNet passing strategies, so verify again once more sooner or later!