 Whereas engaged on an IoT based mostly knowledge acquisition system utilizing well being monitoring sensors, we began visualising this well being monitoring system, which might be worn like an decoration in our everyday life. We thought, what if it’s a sensible gadget that may retailer real-time knowledge, making a platform for each monitoring and analysis for a health care provider whereas we’re in our residence itself. It may have an SOS characteristic, which is among the principal points in India the place individuals are unable to contact hospitals or docs effectively in time.
Whereas engaged on an IoT based mostly knowledge acquisition system utilizing well being monitoring sensors, we began visualising this well being monitoring system, which might be worn like an decoration in our everyday life. We thought, what if it’s a sensible gadget that may retailer real-time knowledge, making a platform for each monitoring and analysis for a health care provider whereas we’re in our residence itself. It may have an SOS characteristic, which is among the principal points in India the place individuals are unable to contact hospitals or docs effectively in time.
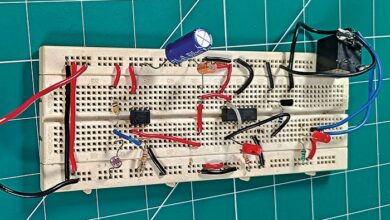
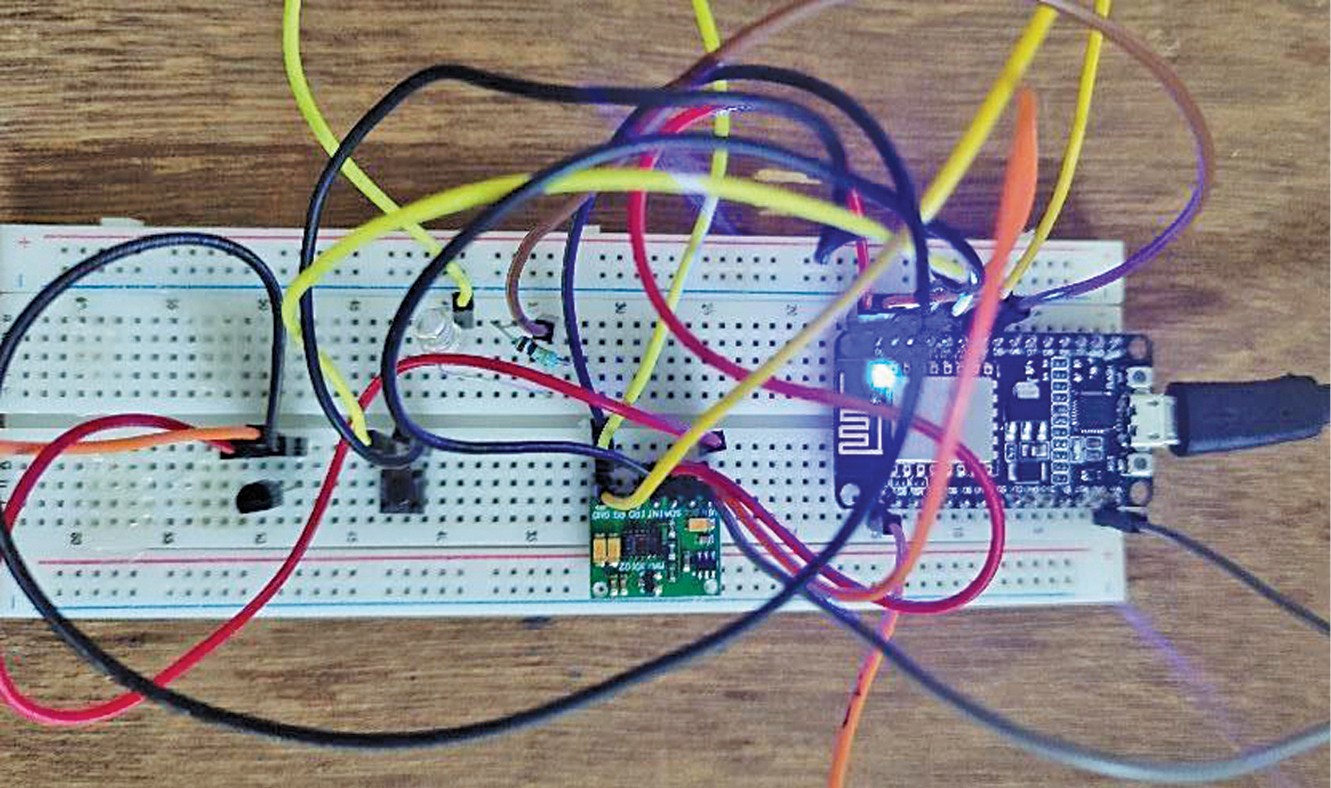
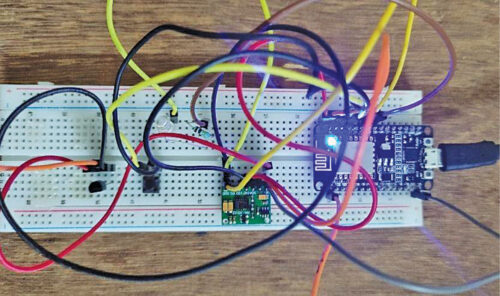
Allow us to try to construct the system that may deal with the above-mentioned issues. A personal channel could be created for the individual whose well being parameters are to be monitored. There could be provision for an SOS emergency indication to alert the physician or some other designated individual. Writer’s prototype of the system on a breadboard is proven in Fig. 1.
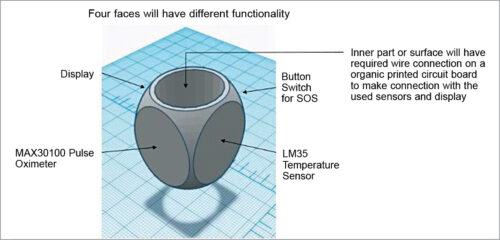
The thought is to surround the entire system in a small-size decoration like a hoop to observe the well being parameters. So, we are able to change the elements within the prototype with small-size elements that may slot in a hoop whose design is of our alternative. The prototype could be designed within the form of a cube formed ring, as proven in Fig. 2 and Fig. 3, or some other sensible form of our alternative.

Circuit and dealing
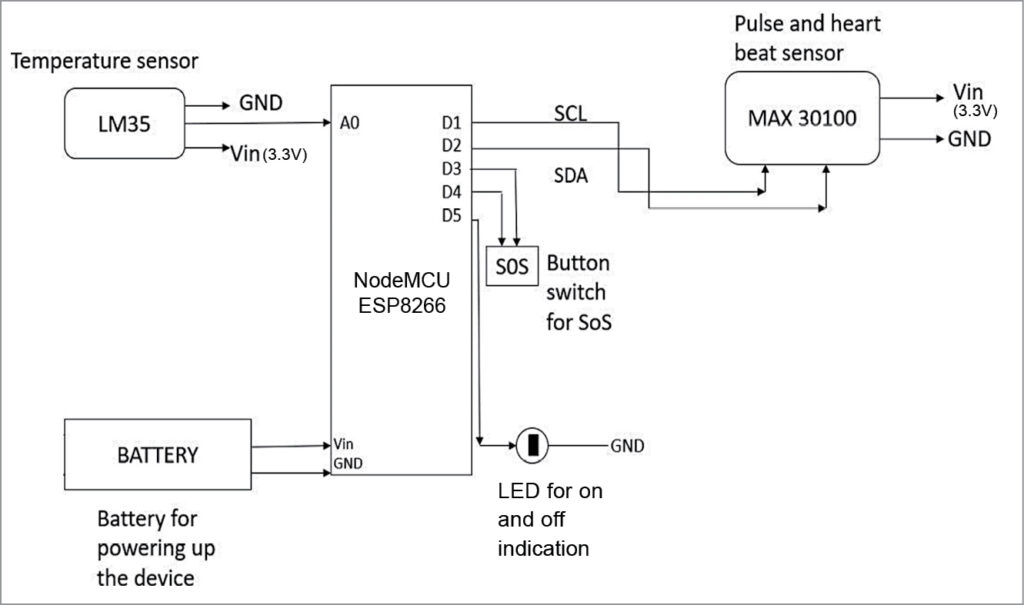
Circuit diagram of the sensible wearable well being monitoring ring constructed round nodemcu ESP8266 microcontroller is proven in Fig. 4. The opposite elements embody MAX30100 pulse oximeter sensor, temperature sensor LM35, a small pushbutton swap for triggering an SOS message, an LED for on/off indication, and a tiny 3.3V battery.
ThingSpeak is used to create the non-public cloud based mostly IoT-enabled monitoring platform with knowledge retrieval functionality. (ThingSpeak is an IoT analytics platform service that lets you mixture, see, and analyse stay knowledge streams within the cloud.) You learn the info from the general public ThingSpeak Channel 12397 Climate Station and write it into your new channel.
You’ll be able to signal into ThingSpeak utilizing your MathWorks account credentials, or create a brand new account. After that click on on Channels> MyChannels, then on Channels web page click on on My Channels, as proven in Fig. 5.
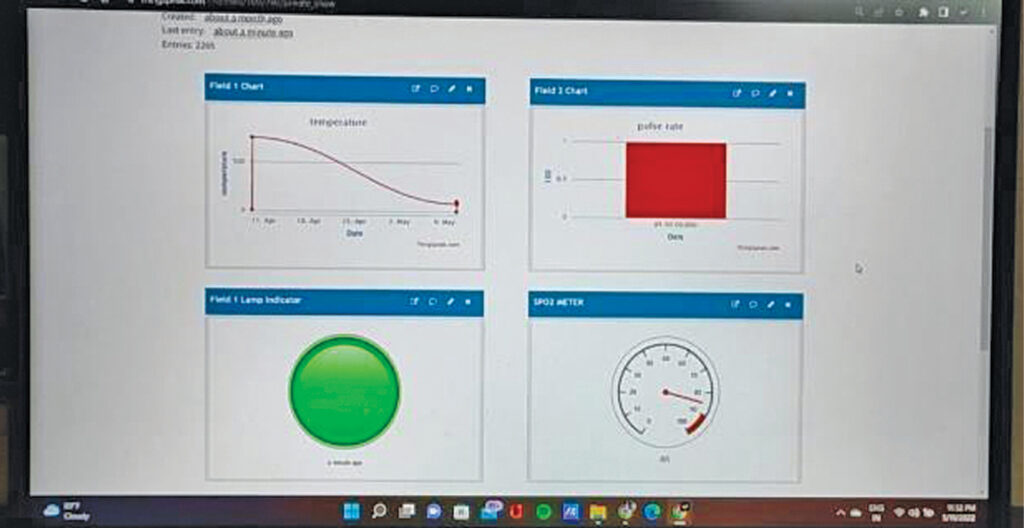
Subsequent, below New Channel, within the containers subsequent to Fields 1, 2, and three, enter the next channel setting values, as proven in Fig. 6:
Identify: Dew Level Measurement
Discipline 1: Temperature (F)
Discipline 2: Humidity
Discipline 3: Dew Level
Subsequent, click on on Save Channel on the backside of the settings. You’ll now see the next tabs:
Non-public View. It shows details about your channel that solely you may see.
Public View. Should you select to make your channel publicly obtainable, use this tab to show chosen fields and channel visualisations.
Channel Settings. It exhibits all of the channel choices you set on the time of creation. You’ll be able to edit, clear, or delete the channel from this tab.
Sharing. It exhibits channel sharing choices. You’ll be able to set a channel as non-public, shared with everybody (public), or shared with particular customers.
API Keys. This tab shows your channel API keys. Use the keys to learn from and write to your channel.
Information Import/Export. This tab allows you to import and export channel knowledge.
You’ll be able to thus create a personal channel as per your requirement after which use the offered API to jot down the info that’s to be exported in several codecs. The information could be extracted in all three codecs: xtml, csv, and json. This knowledge can be utilized in Android based mostly apps, as json format is on the market, and likewise for internet functions. The requisites like SSID code, password, channel title, and the API key ought to be modified when you create a brand new system for a unique individual.

Coding
After the ThingSpeak API and channel setting is completed, create the code to learn sensors’ knowledge and add it to ThingSpeak cloud community in actual time. Within the code, it’s essential to do the SSID and password settings on your community, which could be your cellphone hotspot or residence Wi-Fi community.
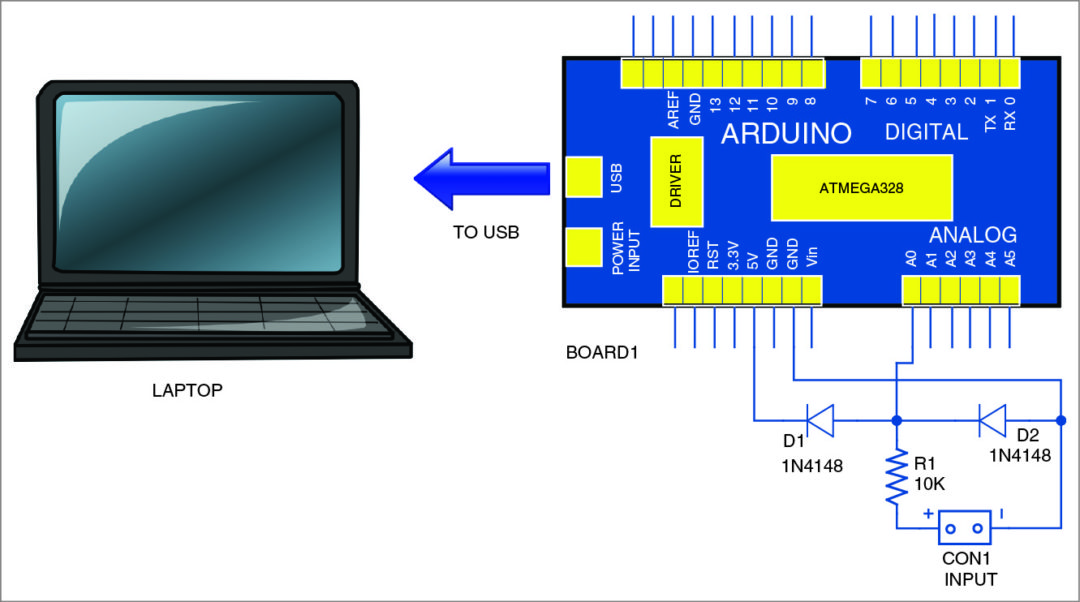
For importing the supply code smart_ring.ino into Arduino Uno board, join the Arduino board to desktop/laptop computer utilizing USB cable. Subsequent, choose the board and port and add the code (smart_ring.ino). You’ll be able to obtain it from the hyperlink
| Invoice of Materials | ||
| Element title | Amount | Description |
| Nodemcu ESP8266 | 1 | Microcontroller to correlate your entire course of and connect with cloud |
| MAX 30100 pulse oximeter sensor | 1 | To measures pulse and spo2 degree |
| Push button | 1 | Change |
| LM35 | 1 | Temperature measuring gadget |
| LED and resistor | 1 every | Indication of motion |
| Jumper wires | As required | Used for connection |
| Lithium-ion battery | 5V/2000mAh | Used to energy the gadget |
Development and testing
Present energy to the assembled circuit with a 5V USB adaptor or some other 5V DC regulated energy provide after which watch for a couple of seconds, until the circuit connects to Wi-Fi. Now open the ThingSpeak channel you could have created; you may see your well being knowledge in actual time.
Whenever you place a finger on the MAX30100 sensor, it’s going to begin exhibiting your pulse fee, oxygen proportion in blood, and temperature of your physique in actual time on the ThingSpeak channel. Whenever you press the SOS button, you may see the state of SOS button in actual time from any gadget anyplace.
This futuristic gadget could be helpful for everybody, particularly so for the previous and infirm, the sick and bedridden, and the pregnant girls, all of whom want particular care and a spotlight. It could possibly scale back their journeys to the physician or a hospital because the very important well being parameters can now be seen remotely. Welcome to the brand new age of well being monitoring!
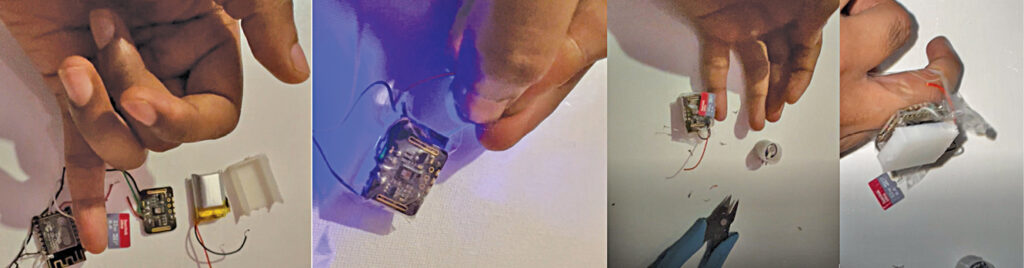
Throughout meeting, the ESP8266 NodeMCU is changed with ESP 8266 chip and all different sensors and elements could be mounted into the small ring, as proven within the Fig. 8.
Obtain supply code
Duraiarasu. E is B.E in Electronics and Communications Engineering (ECE). His areas of curiosity embody Embedded Programs, VLSI, IoT, Robotics and Automation, and Machine Studying